How to easily inspect and modify network traffic
You’re more of a video kind of person? I’ve got you covered! Here’s a video with the same content than this article 🍿
Advertisement
Debug HTTP/HTTPS with Proxyman like a Pro
Try Proxyman, a native macOS app that captures and displays Request/Response in beautiful UIs.
Supports iOS and Android, both devices and simulators.
Sponsors like Proxyman really help me grow my content creation, so if you have time please make sure to check out their product: it’s a direct support to my content creation ☺️
In this article, I want to show you how you can intercept HTTPS traffic, so that you can inspect it and even modify it.
To do this, we're going to use a nice little app called Proxyman.
Now, full disclosure, this email has been sponsored by Proxyman.
However, all the features I'm gonna show you are available for free in the app: you don't need to pay anything to use them.
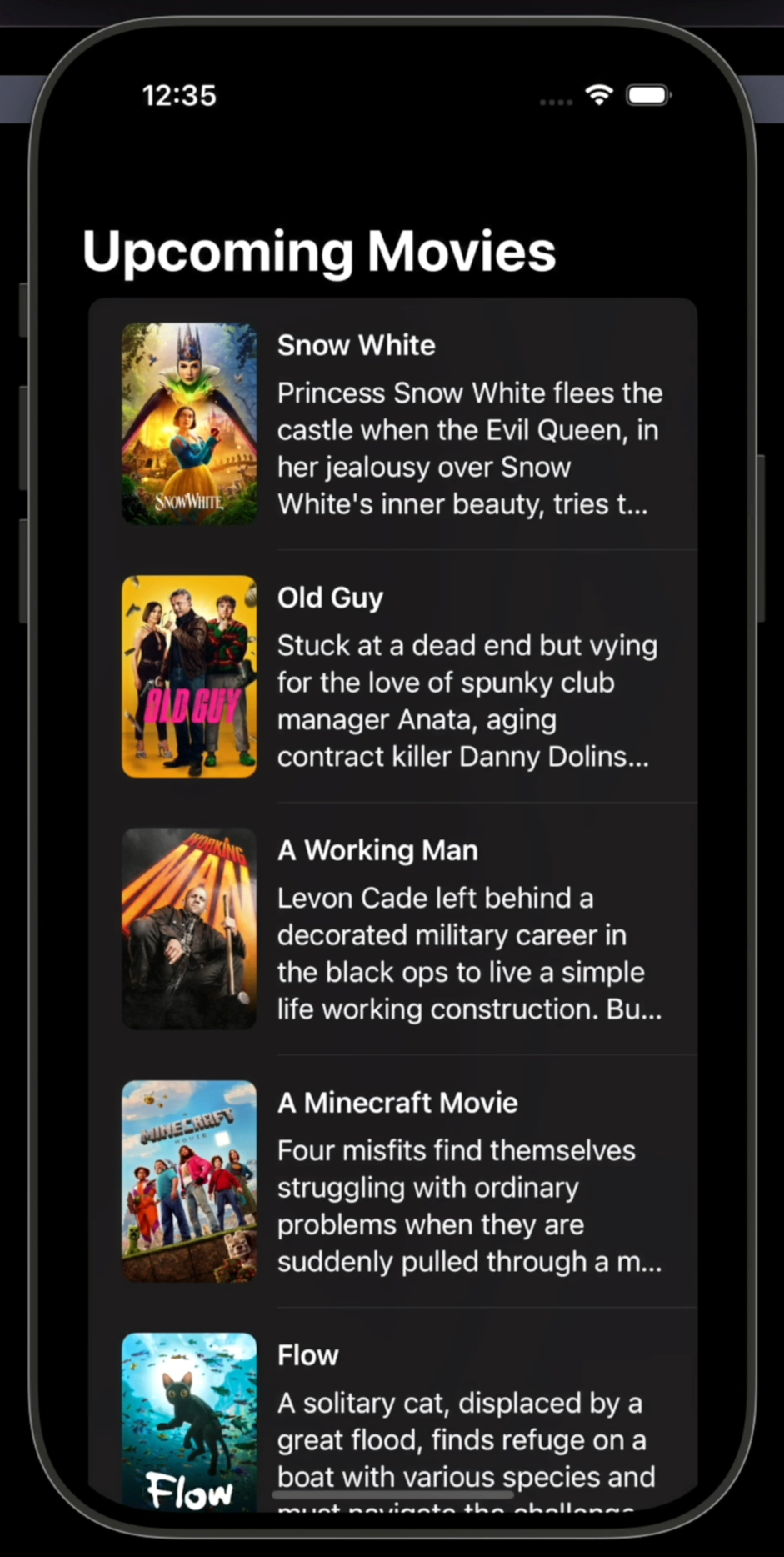
As you can see, I've implemented a simple SwiftUI app that queries an API to fetch and display a list of upcoming movies:
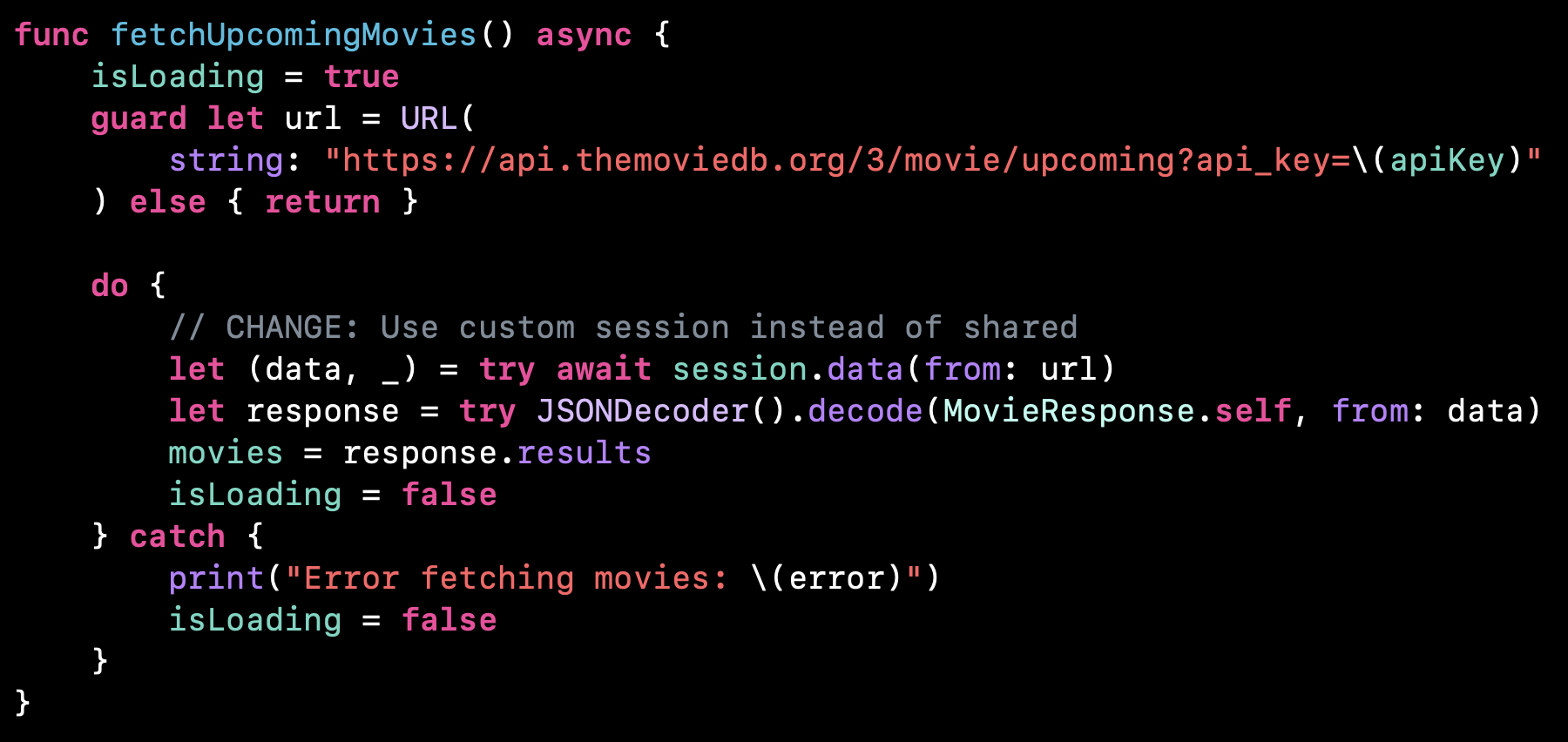
And if we look at the code that makes the network call, we can see that the API call uses HTTPS:
This should make it harder for us to intercept and inspect the network call, because HTTPS means that the network traffic is being encrypted.
But as we're going to see, by using Proxyman, it's gonna be actually fairly easy to see the details of the traffic.
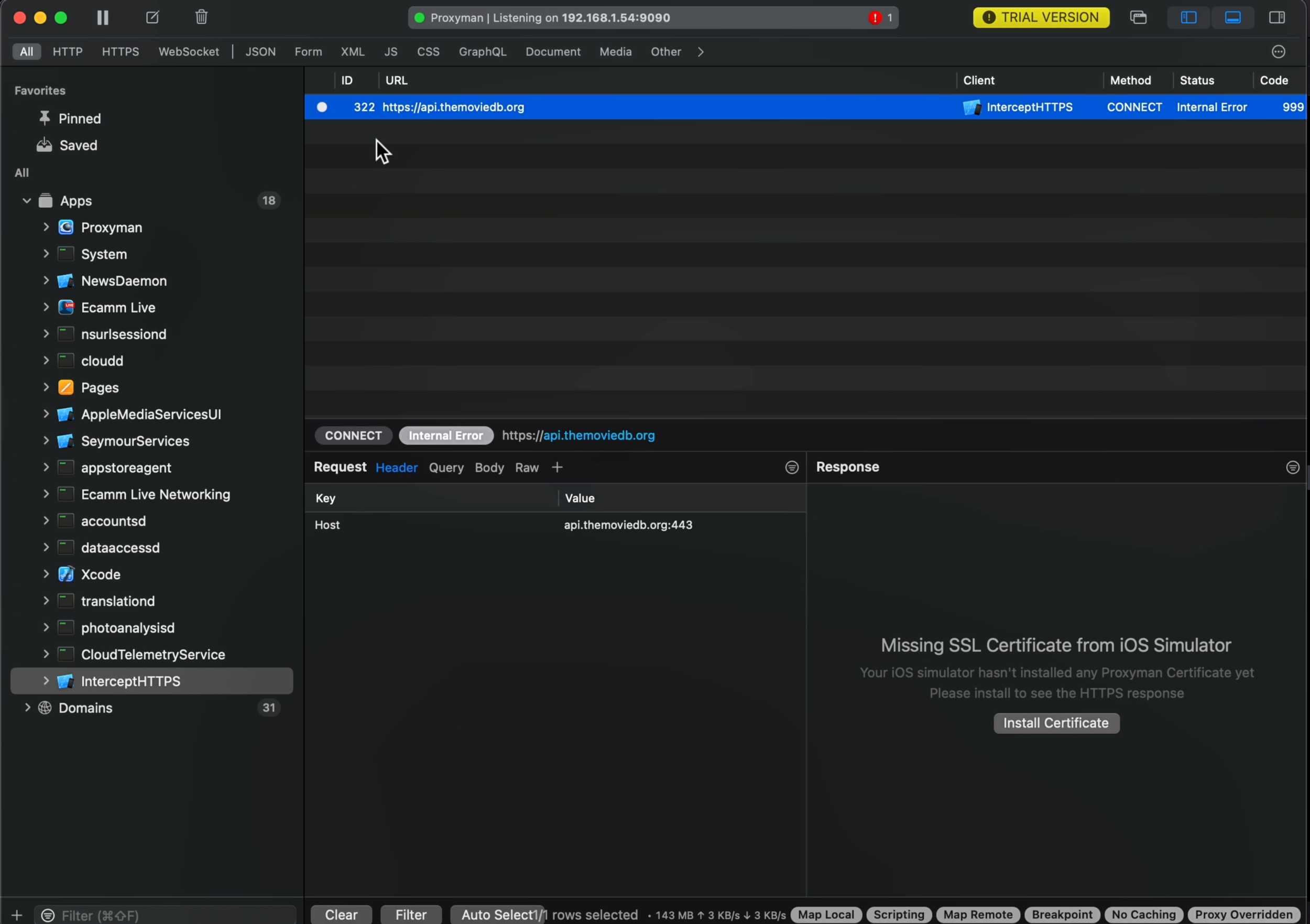
So let’s open Proxyman and inspect the network traffic:
We can see that the network call now produces an Internal Error.
This might seem weird but it’s actually totally normal.
The reason is that Proxyman is putting itself in the middle between our app and the backend that the app is making requests to.
The thing is, this is what's also known as a man-in-the-middle attack.
Here it’s being used in a legitimate way, we're inspecting our own app, but this technique could be used by an adversary in order to hack your app.
So it's totally normal that iOS blocks it by default!
However, since we want to allow the interception, we’re going to click on Install Certificate and follow the procedure:
And once that’s done, we’ll just need to relaunch the app and we’ll see that now Proxyman is able to intercept the HTTPS traffic:
What’s really nice here is that we’re able to fully inspect the network traffic of the app without having made a single change to its code!
If you’re used to adding logs to the console when you want to debug a network issue, this approach should already be quite a good time saver.
But it gets even better: we can also modify the traffic!
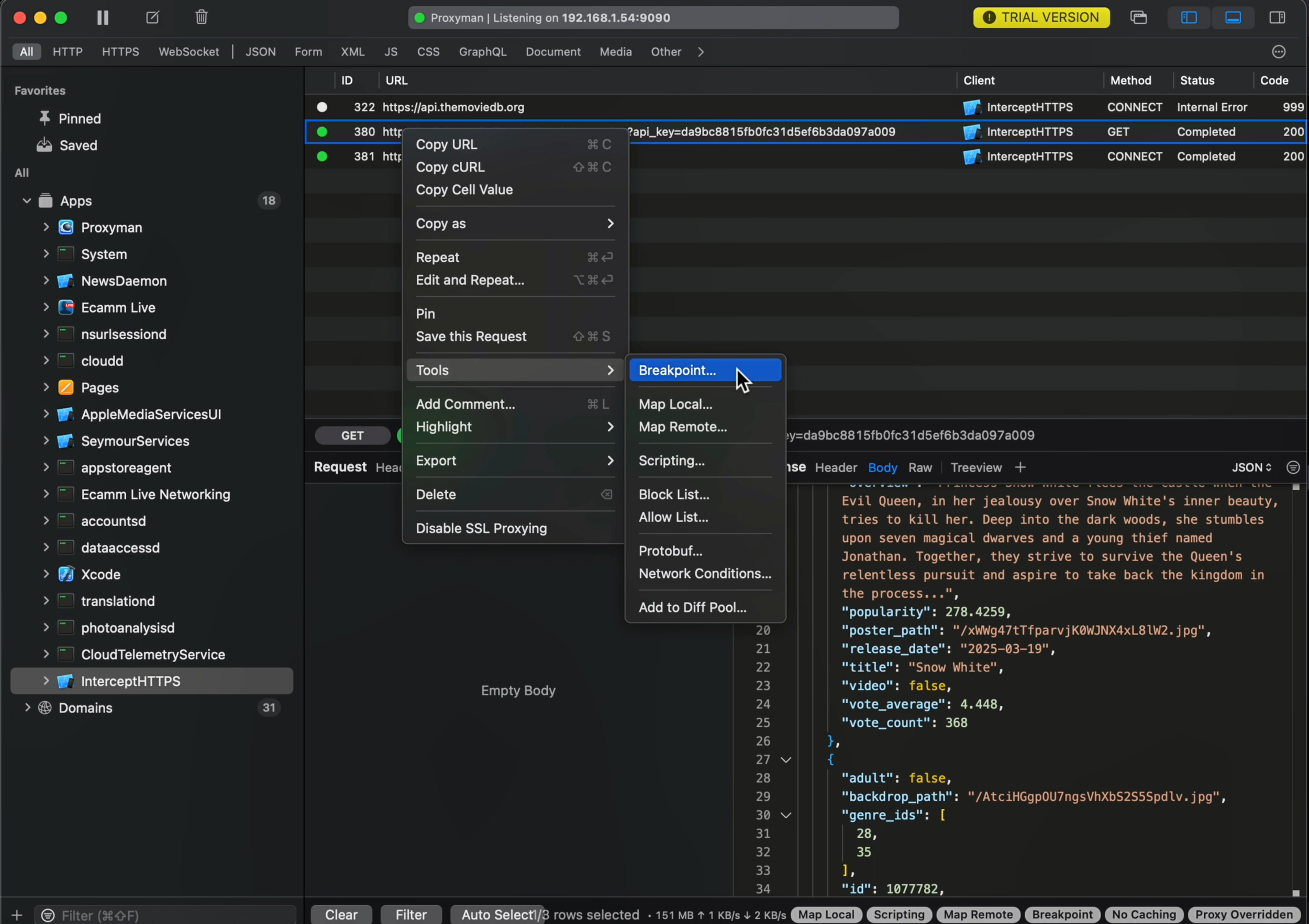
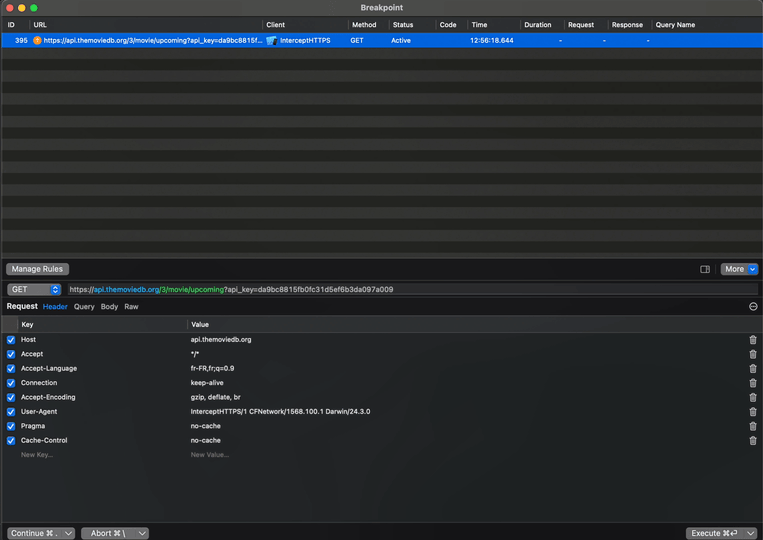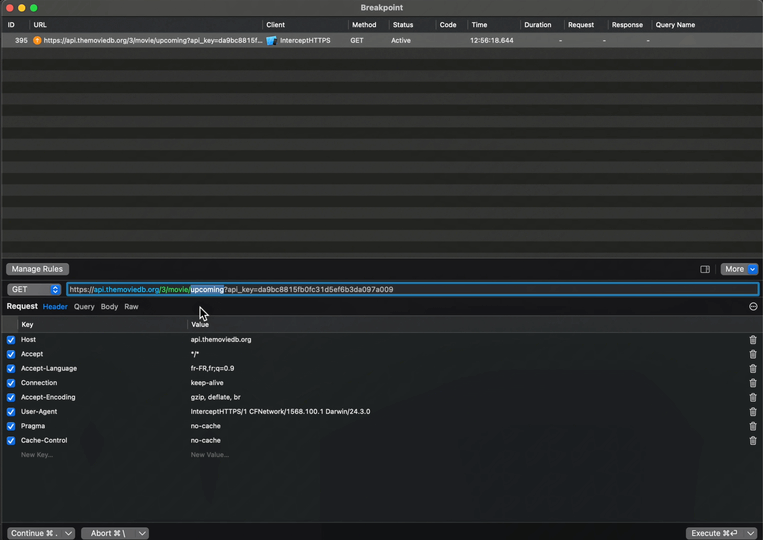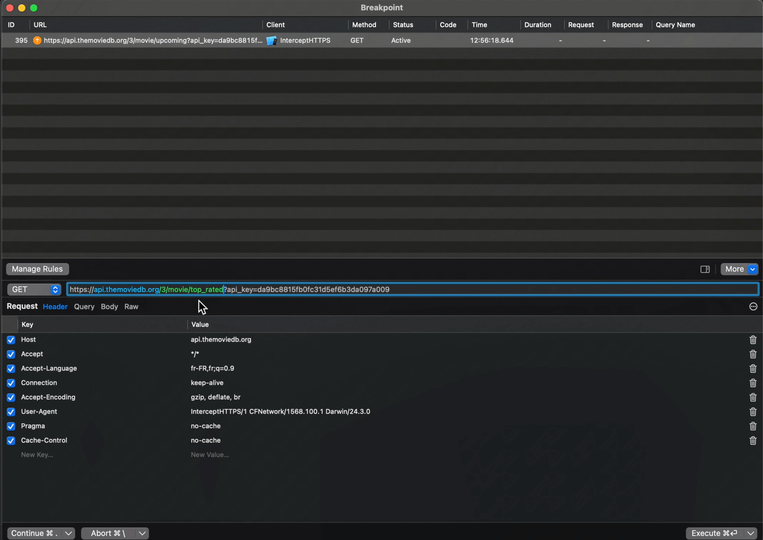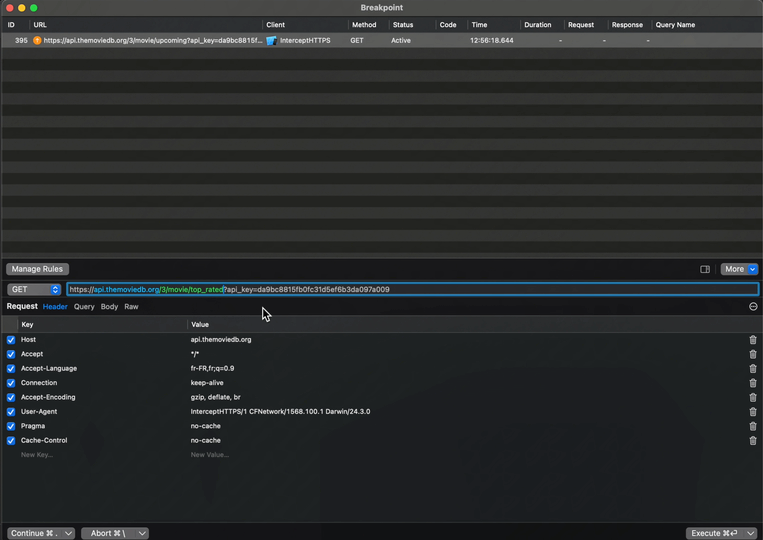
For this, we’ll need to set a breakpoint on the network call:
This breakpoint works very similarly to one that you would set in Xcode: it will trigger whenever the same request is performed again.
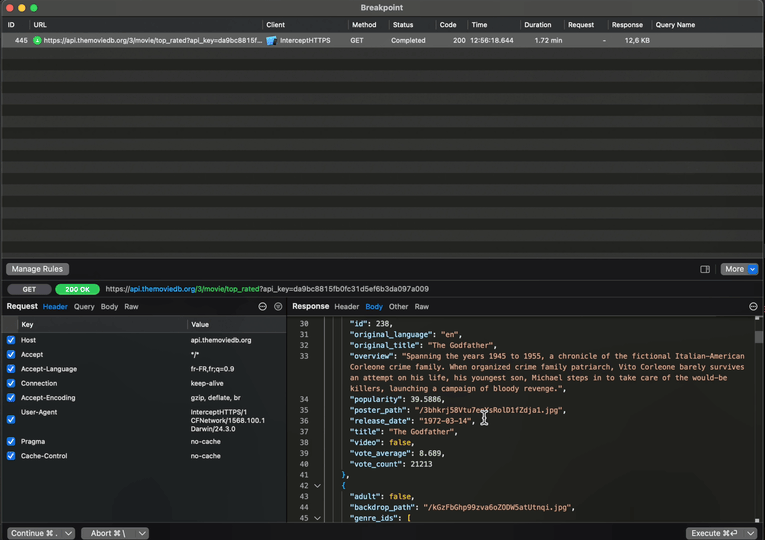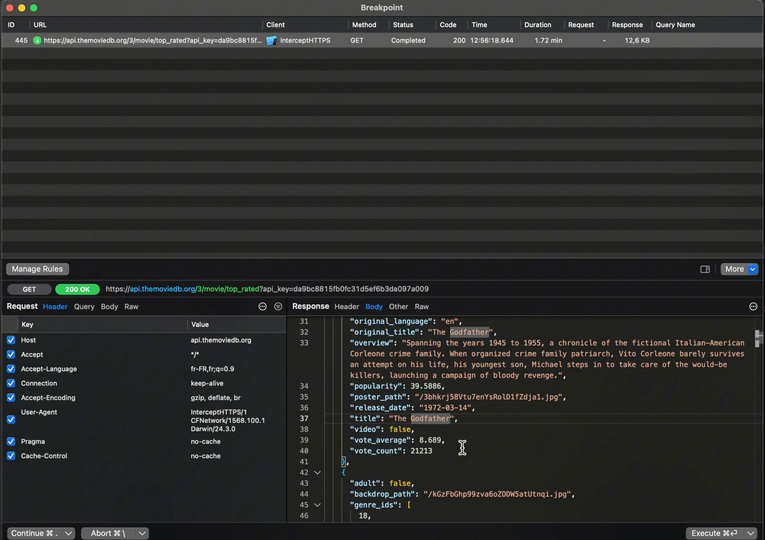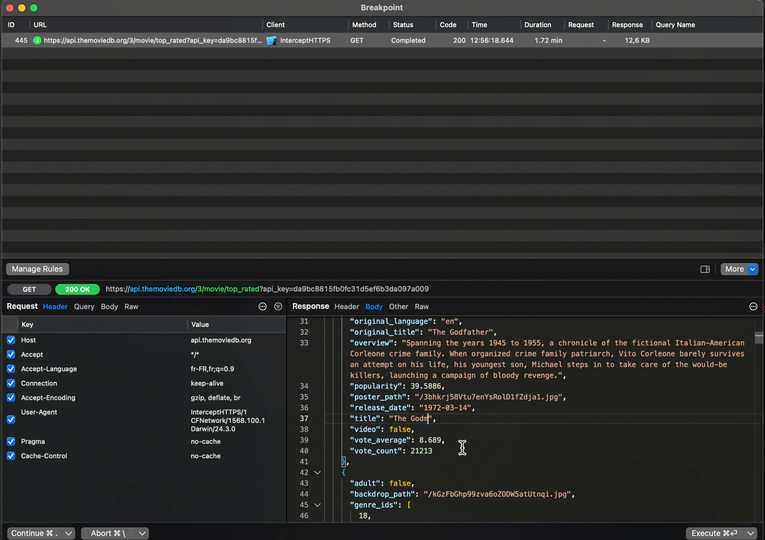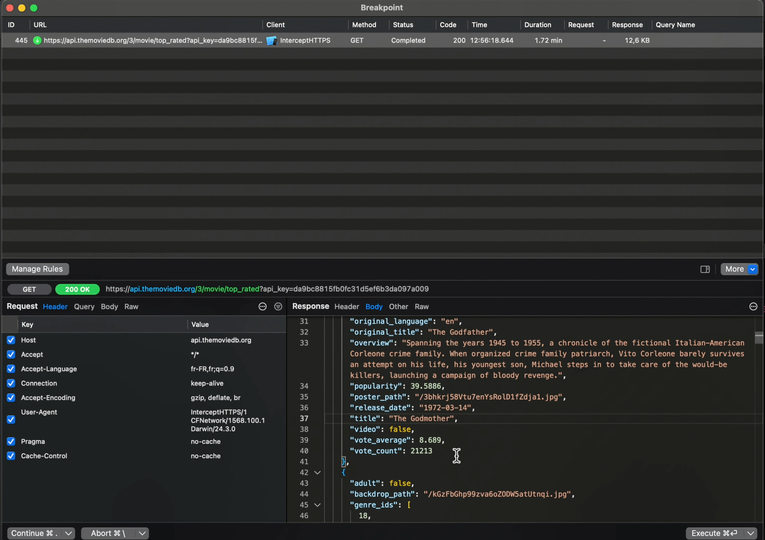
And when the breakpoint triggers, you’ll see this screen, where you can inspect the outgoing request but also modify it:
And as you can imagine, you can also do the exact same thing with the incoming response:
Finally, when the execution resumes, we can see that the data our app has received is indeed the one the we’ve modified:
With this feature, it becomes possible to easily inject a response that corresponds to a tricky edge case of your app.
And doing it by using Proxyman to modify the network traffic is likely to be much faster than trying to trigger such a complex edge case manually.
And that covers what I wanted to show you!
As we’ve seen, Proxyman is a pretty useful tool, that allows you to intercept, inspect and even modify the network traffic of your app.
All that without requiring a single change to the actual code base.